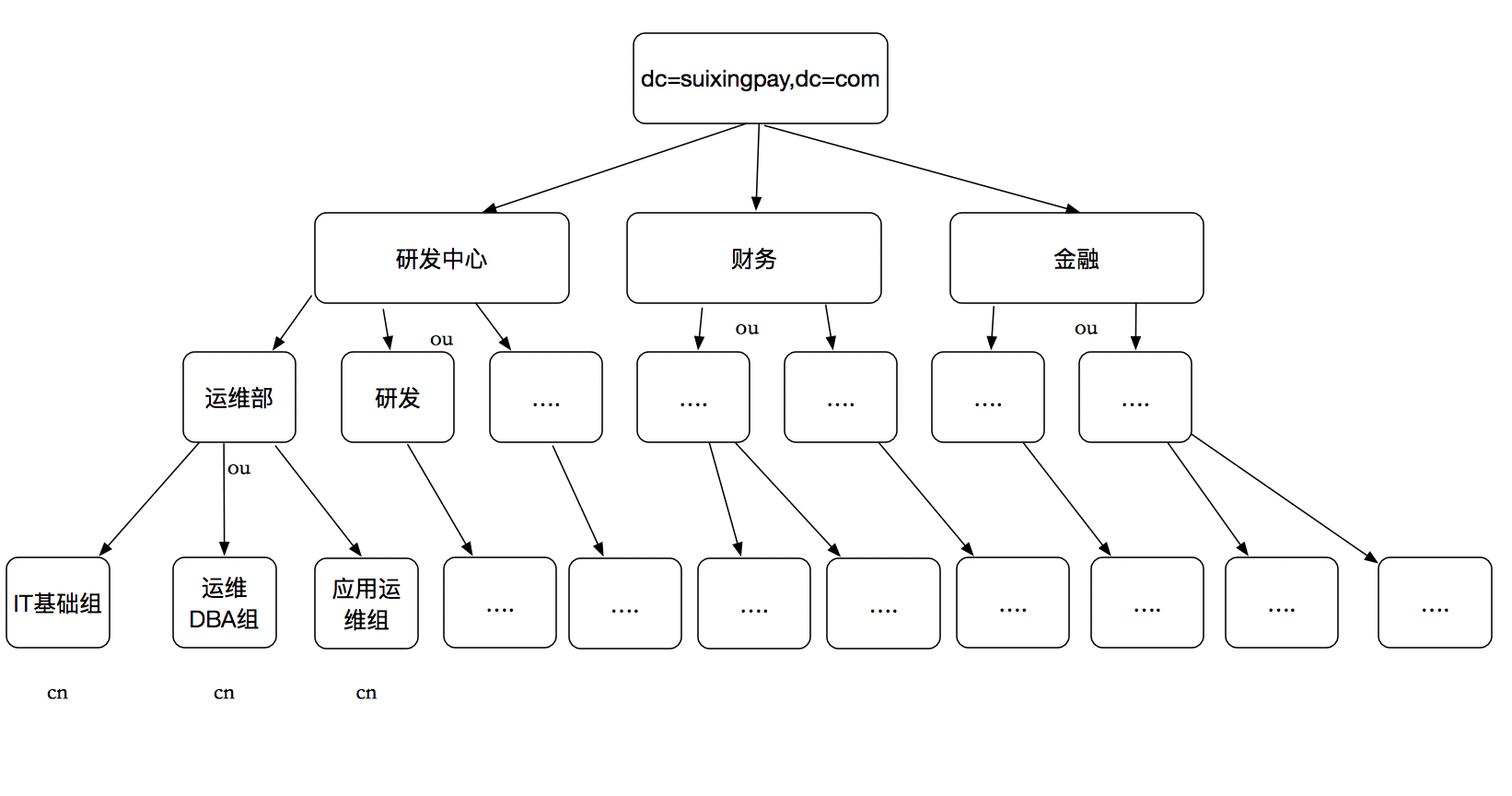
1 OpenLDAP简介
LDAP 全称轻量级目录访问协议(英文:Lightweight Directory Access Protocol),是一个运行在 TCP/IP 上的目录访问协议。LDAP实现提供被称为目录服务的信息服务,可以看做是一张特殊的数据库系统。可以有效的解决众多网络服务的用户账户问题,规定了统一的身份信息数据库、身份认证机制和接口,实现了资源和信息的统一管理,保证了数据的一致性和完整性。
OpenLDAP 目录服务优点
OpenLDAP 目录服务有以下10 个优点。
OpenLDAP 是一个跨平台的标准互联网协议,它基于X.500 标准协议。
OpenLDAP 提供静态数据查询搜索,不需要像在关系数据中那样通过SQL 语句维护数据库信息。
OpenLDAP 基于推和拉的机制实现节点间数据同步,简称复制(replication)并提供基于TLS、SASL 的安全认证机制,实现数据加密传输以及Kerberos 密码验证功能。
OpenLDAP 可以基于第三方开源软件实现负载(LVS、HAProxy)及高可用性解决方案,24 小时提供验证服务,如Headbeat、Corosync、Keepalived 等。
OpenLDAP 数据元素使用简单的文本字符串(简称LDIF 文件)而非一些特殊字符,便于维护管理目录树条目。
OpenLDAP 可以实现用户的集中认证管理,所有关于账号的变更,只须在OpenLDAP 服务器端直接操作,无须到每台客户端进行操作,影响范围为全局。
OpenLDAP 默认使用协议简单如支持TCP/ZP 协议传输条目数据,通过使用查找操作实现对目录树条目信息的读写操作,同样可以通过加密的方式进行获取目录树条目信息。
OpenLDAP 产品应用于各大应用平台(Nginx、HTTP、vsftpd、Samba、SVN、Postfix、OpenStack、Hadoop 等)、服务器(HP、IBM、Dell 等)以及存储(EMC、NetApp 等)控制台,负责管理账号验证功能,实现账号统一管理。
OpenLDAP 实现具有费用低、配置简单、功能强大、管理容易及开源的特点。
OpenLDAP 通过ACL(Access Control List)灵活控制用户访问数据的权限,从而保证数据的安全性。
2.环境准备
2.1 服务器规划
| ip | hostname | 说明 |
|---|---|---|
| 192.168.123.23 | openldap-server | server端 |
| 192.168.123.63 | openldap-client | client端 |
2.2 关闭SELinux
[root@localhost ~]# setenforce 0
setenforce: SELinux is disabled
[root@localhost ~]# sed -i 's#SELINUX=enforcing#SELINUX=disabled#g' /etc/selinux/config
[root@localhost ~]# grep SELINUX=disabled /etc/selinux/config
SELINUX=disabled
2.3 修改主机名
hostnamectl set-hostname openldap-server
hostnamectl set-hostname openldap-client
2.4 关闭iptables
查看防火墙状态
firewall-cmd --state
停止firewall
systemctl stop firewalld.service
禁止firewall开机启动
systemctl disable firewalld.service
2.5 系统环境信息
[root@localhost ~]# cat /etc/redhat-release
CentOS Linux release 7.4.1708 (Core)
[root@localhost ~]# uname -a
Linux localhost.localdomain 3.10.0-693.el7.x86_64 #1 SMP Tue Aug 22 21:09:27 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
[root@localhost ~]# uname -r
3.10.0-693.el7.x86_64
3 server端安装OpenLDAP
3.1 yum安装OpenLDAP
yum -y install openldap compat-openldap openldap-clients openldap-servers openldap-servers-sql openldap-devel
查看安装的版本:
[root@openldap-server02 ~]# slapd -VV
@(#) OpenLDAP: slapd 2.4.44 (Jan 29 2019 17:42:45)
mockbuild@x86-01.bsys.centos.org:/builddir/build/BUILD/openldap-2.4.44/openldap-2.4.44/servers/slapd
3.2 配置OpenLDAP
3.2.1 设置LDAP管理密码
[root@openldap-server ~]# slappasswd -s 123456
{SSHA}as8n5Ts2oGhnFVtW3sI8hloDFui8JB3Z
3.2.2 配置OpenLDAP数据库
cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
chown ldap:ldap /var/lib/ldap/*
3.2.3 添加需要的schemas
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
3.2.4 启动和开机自启及验证
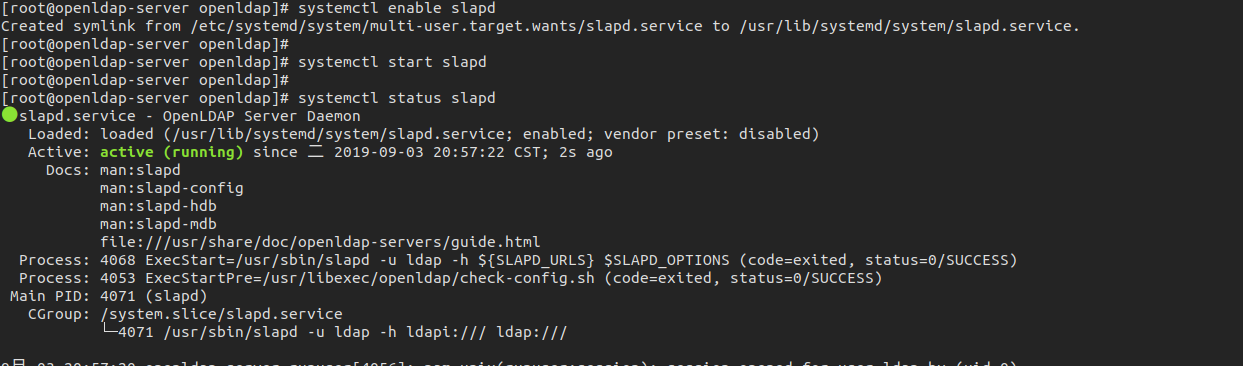
systemctl start slapd.service
systemctl enable slapd.service
验证
[root@openldap-server openldap]# netstat -antup | grep -i 389
tcp 0 0 0.0.0.0:389 0.0.0.0:* LISTEN 13337/slapd
tcp6 0 0 :::389 :::* LISTEN 13337/slapd
3.2.5 配置openLDAP服务config
cat config.ldif
dn: olcDatabase={1}monitor,cn=config
changetype: modify
replace: olcAccess
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external, cn=auth" read by dn.base="cn=Manager,dc=devopstack,dc=com" read by * none
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcSuffix
olcSuffix: dc=devopstack,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootDN
olcRootDN: cn=Manager,dc=devopstack,dc=com
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootPW
olcRootPW: {SSHA}0NLFekBuJUuT9/U2JNWV0rmi6640Xn/B
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcAccess
olcAccess: {0}to attrs=userPassword,shadowLastChange by dn="cn=Manager,dc=devopstack,dc=com" write by anonymous auth by self write by * none
olcAccess: {1}to dn.base="" by * read
olcAccess: {2}to * by dn="cn=Manager,dc=devopstack,dc=com" write by * read
# 发送配置到LDAP服务
ldapmodify -Y EXTERNAL -H ldapi:/// -f config.ldif
其中cn=Manager中的Manager表示OpenLDAP管理员的用户名,而olcRootPW表示OpenLDAP管理员的密码。
3.3 域devopstack配置
vi base.ldif
[root@openldap-server ~]# cat base.ldif
dn: dc=devopstack,dc=com
o: devopstack com
dc: devopstack
objectClass: top
objectClass: dcObject
objectClass: organization
dn: cn=Manager,dc=devopstack,dc=com
objectClass: organizationalRole
cn: Manager
description: LDAP Manager
dn: ou=People,dc=devopstack,dc=com
objectClass: organizationalUnit
ou: People
dn: ou=Group,dc=devopstack,dc=com
objectClass: organizationalUnit
ou: Group
# 发送配置到LDAP服务
ldapadd -x -W -D "cn=Manager,dc=devopstack,dc=com" -f base.ldif
[root@openldap-server ~]# ldapadd -x -W -D "cn=Manager,dc=devopstack,dc=com" -f base.ldif
Enter LDAP Password:
adding new entry "dc=devopstack,dc=com"
adding new entry "cn=Manager,dc=devopstack,dc=com"
adding new entry "ou=People,dc=devopstack,dc=com"
adding new entry "ou=Group,dc=devopstack,dc=com"
3.4 创建一个测试用户
vi demo.ldif
cat demo.ldif
dn: uid=test01,ou=People,dc=devopstack,dc=com
objectClass: top
objectClass: account
objectClass: posixAccount
objectClass: shadowAccount
cn: test01
uid: test01
uidNumber: 30001
gidNumber: 80001
homeDirectory: /home/test01
loginShell: /bin/bash
gecos: Demo [Demo user (at) devopstack]
userPassword: {crypt}x
shadowLastChange: 17058
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
dn: cn=ops,ou=Group,dc=devopstack,dc=com
objectClass: posixGroup
objectClass: top
cn: ops
gidNumber: 80001
# 创建
[root@openldap-server ~]# ldapadd -x -W -D "cn=Manager,dc=devopstack,dc=com" -f demo.ldif
Enter LDAP Password:
adding new entry "uid=test01,ou=People,dc=devopstack,dc=com"
adding new entry "cn=ops,ou=Group,dc=devopstack,dc=com"
# 改密
[root@openldap-server ~]# ldappasswd -s 'passwd@123' -W -D "cn=Manager,dc=devopstack,dc=com" -x "uid=test01,ou=People,dc=devopstack,dc=com"
Enter LDAP Password: 123456
# 验证搜索
ldapsearch -x uid=test01 -b dc=devopstack,dc=com
# extended LDIF
#
# LDAPv3
# base <dc=devopstack,dc=com> with scope subtree
# filter: uid=test01
# requesting: ALL
#
# test02, People, devopstack.com
dn: uid=test02,ou=People,dc=devopstack,dc=com
objectClass: top
objectClass: account
objectClass: posixAccount
objectClass: shadowAccount
cn: test02
uid: test01
uid: test02
uidNumber: 3001
gidNumber: 80001
homeDirectory: /home/test02
loginShell: /bin/bash
gecos: Demo [Demo user (at) devopstack]
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
//删除使用如下命令,暂不删除,因后续实验需用到测试用户
ldapdelete -W -D "cn=Manager,dc=devopstack,dc=com" -x "uid=test01,ou=People,dc=devopstack,dc=com"
3.5 启用LDAP日志记录
# 配置ldap log
vim loglevel.ldif
dn: cn=config
changetype: modify
replace: olcLogLevel
olcLogLevel: stats
# 发送配置到LDAP服务
ldapmodify -Y EXTERNAL -H ldapi:/// -f loglevel.ldif
echo "local4.* /var/log/slapd/slapd.log" >> /etc/rsyslog.conf
vi /etc/logrotate.d/slapd
/var/log/openldap.log {
rotate 14
size 10M
missingok
compress
copytruncate
}
systemctl restart rsyslog
# 如果有需要还可以配置日志轮转
3.6 安装openLdap web端服务
3.6.1 安装phpldapadmin
yum安装httpd及PhpLdapAdmin
yum install -y epel*
yum install httpd phpldapadmin -y
3.6.2 配置phpldapadmin及php
配置/etc/httpd/conf.d/phpldapadmin.conf允许从远程访问
cp -a /etc/httpd/conf.d/phpldapadmin.conf{,.bak}
cat /etc/httpd/conf.d/phpldapadmin.conf
#
# Web-based tool for managing LDAP servers
#
Alias /phpldapadmin /usr/share/phpldapadmin/htdocs
Alias /ldapadmin /usr/share/phpldapadmin/htdocs
<Directory /usr/share/phpldapadmin/htdocs>
Order Deny,Allow
Allow from all
</Directory>
修改/etc/phpldapadmin/config.php配置用DN登录
cp /etc/phpldapadmin/config.php{,.bak}
vim /etc/phpldapadmin/config.php
//servers->setValue('login','attr','uid');servers->setValue('login','attr','dn');
修改/etc/httpd/conf/httpd.conf
cat /etc/httpd/conf/httpd.conf
<Directory />
Options Indexes FollowSymLinks
AllowOverride none
</Directory>
3.6.3 启动httpd及验证服务
启动httpd服务
service httpd start
service httpd status
3.7 新建组织(公司)管理员组及用户
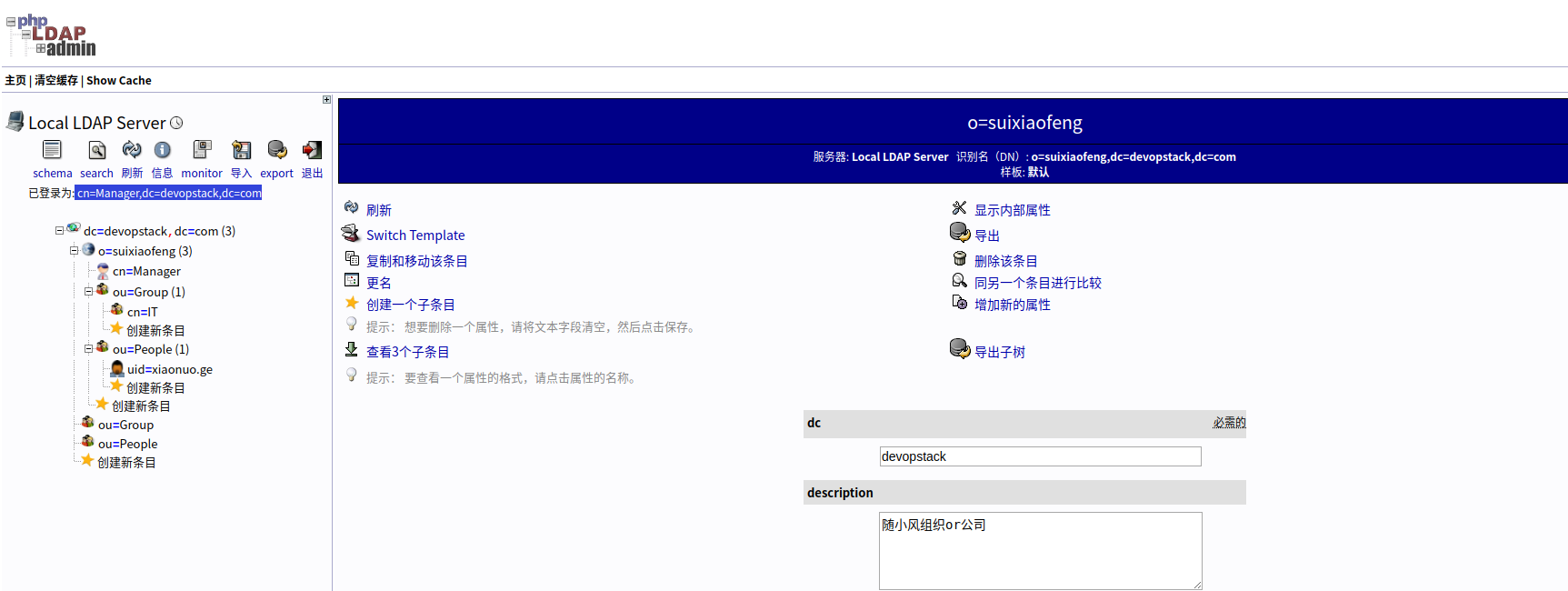
3.7.1 创建组织
cat o.ldif
dn: o=suixiaofeng,dc=devopstack,dc=com
objectclass: top
objectclass: dcobject
objectclass: organization
dc: devopstack
o: suixiaofeng
description: 随小风组织or公司
street: 地址
导入组织数据
ldapadd -x -w "123456" -D "cn=Manager,dc=devopstack,dc=com" -f o.ldif
adding new entry "o=suixiaofeng,dc=devopstack,dc=com"
查看导入结果:
ldapsearch -x -b "o=suixiaofeng,dc=devopstack,dc=com" -H ldap://127.0.0.1
# extended LDIF
#
# LDAPv3
# base <o=suixiaofeng,dc=devopstack,dc=com> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# suixiaofeng, devopstack.com
dn: o=suixiaofeng,dc=devopstack,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
dc: devopstack
o: suixiaofeng
description:: 6ZqP5bCP6aOO57uE57uHb3Llhazlj7gg
street:: 5Zyw5Z2A
3.7.2 创建管理员及组
在suixiaofeng组织下创建一个 Manager 的组织角色(该角色内的用户具有管理整个 LDAP 的权限)和 People 和 Group 两个组织单元:
cat admin_group.ldif
dn: cn=Manager,o=suixiaofeng,dc=devopstack,dc=com
objectClass: organizationalRole
cn: Manager
dn: ou=Group,o=suixiaofeng,dc=devopstack,dc=com
ou: Group
objectClass: organizationalUnit
dn: ou=People,o=suixiaofeng,dc=devopstack,dc=com
ou: People
objectClass: organizationalUnit
导入组数据
ldapadd -x -w "123456" -D "cn=Manager,dc=devopstack,dc=com" -f admin_group.ldif
adding new entry "cn=Manager,o=suixiaofeng,dc=devopstack,dc=com"
adding new entry "ou=Group,o=suixiaofeng,dc=devopstack,dc=com"
adding new entry "ou=People,o=suixiaofeng,dc=devopstack,dc=com"
3.7.3 创建用户及部门(cn组)
设置用户密码
slappasswd -s gexiaonuo
{SSHA}tFxFB4Q3HFyFbMiJnlugnSpilV9CSjCY
cat adduser.ldif
# create new
# replace to your own domain name for "dc=***,dc=***" section
dn: uid=xiaonuo.ge,ou=People,o=suixiaofeng,dc=devopstack,dc=com
objectClass: top
objectclass: person
#objectclass: organizationalPerson
objectclass: inetOrgPerson
objectClass: shadowAccount
uid: xiaonuo.ge
cn: xiaonuo.ge
sn: ge
displayName: 葛小诺
ou: People
description: 可视化
#userPassword: ldappassword
userPassword: {SSHA}tFxFB4Q3HFyFbMiJnlugnSpilV9CSjCY
mail: xiaonuo.ge@devopstack.com
dn: cn=IT,ou=Group,o=suixiaofeng,dc=devopstack,dc=com
objectClass: top
objectClass: groupOfUniqueNames
cn: IT
uniquemember: uid=xiaonuo.ge,ou=People,o=suixiaofeng,dc=devopstack,dc=com
导入用户数据
ldapadd -x -w "123456" -D "cn=Manager,dc=devopstack,dc=com" -f adduser.ldif
adding new entry "uid=xiaonuo.ge,ou=People,o=suixiaofeng,dc=devopstack,dc=com"
adding new entry "cn=IT,ou=Group,o=suixiaofeng,dc=devopstack,dc=com"
4 OpenLDAP客户端的配置
4.1 安装LDAP client
yum install nss-pam-ldapd openldap-clients openldap -y
4.2 配置LDAP client
4.3 重启服务nslcd
systemctl restart nslcd
systemctl restart sshd
4.4 添加新组新账号
添加新账号
[root@openldap-server ~]# cat adduser1.ldif
dn: uid=test03,ou=People,dc=devopstack,dc=com
uid: test03
cn: test03
objectClass: account
objectClass: posixAccount
objectClass: top
objectClass: shadowAccount
userPassword: {SSHA}/+M0+C3pbJr8KayEbtbGKMDGlkSmbcb8
shadowLastChange: 17417
shadowMin: 0
shadowMax: 99999
shadowWarning: 7
loginShell: /bin/bash
uidNumber: 1001
gidNumber: 1000
homeDirectory: /home/test03
命令导入:
ldapadd -x -w "123456" -D "cn=Manager,dc=devopstack,dc=com" -f adduser1.ldif
adding new entry "uid=test03,ou=People,dc=devopstack,dc=com"
添加新组
cat addgroup.ldif
dn: cn=ops,ou=Group,dc=devopstack,dc=com
objectClass: posixGroup
objectClass: top
cn: ops
memberUid: test01
userPassword:
gidNumber: 1000
命令导入:
ldapadd -x -w "123456" -D "cn=Manager,dc=devopstack,dc=com" -f addgroup.ldif
4.5 验证账号SSH登录LDAP客户端
5 authconfig备份还原
authconfig --savebackup=openldap.bak (备份)
authconfig --restorebackup=openldap.bak (还原)
配置可用如下命令
authconfig --enableldap --enableldapauth --ldapserver=ldap://192.168.123.23 --disableldaptls --enablemkhomedir --ldapbasedn="dc=devopstack,dc=com" --update
6 开启memberOf
默认情况下openldap的用户组属性是Posixgroup,Posixgroup用户组属性和用户没有实际的对应关系。如果要对应起来的话,就需要单独把用户设置到Posixgroup中
开启memberOf之后可以配置groupOfUniqueNames用户组属性,可以根据用户组过滤用户,这个过滤是唯一的
开启memberof,并让新增用户支持memberof
创建 memberof_config.ldif
[root@openldap-server ~]# cat memberof_config.ldif
dn: cn=module{0},cn=config
cn: modulle{0}
objectClass: olcModuleList
objectclass: top
olcModuleload: memberof.la
olcModulePath: /usr/lib64/openldap
dn: olcOverlay={0}memberof,olcDatabase={2}hdb,cn=config
objectClass: olcConfig
objectClass: olcMemberOf
objectClass: olcOverlayConfig
objectClass: top
olcOverlay: memberof
olcMemberOfDangling: ignore
olcMemberOfRefInt: TRUE
olcMemberOfGroupOC: groupOfNames
olcMemberOfMemberAD: member
olcMemberOfMemberOfAD: memberOf
创建 refint1.ldif
dn: cn=module{0},cn=config
add: olcmoduleload
olcmoduleload: refint
创建 refint2.ldif
dn: olcOverlay=refint,olcDatabase={2}hdb,cn=config
objectClass: olcConfig
objectClass: olcOverlayConfig
objectClass: olcRefintConfig
objectClass: top
olcOverlay: refint
olcRefintAttribute: memberof member manager owner
导入配置
ldapadd -Q -Y EXTERNAL -H ldapi:/// -f memberof_config.ldif
ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f refint1.ldif
ldapadd -Q -Y EXTERNAL -H ldapi:/// -f refint2.ldif
验证一下配置,这个命令可以列出所有配置
slapcat -b cn=config
7 配置LDAP sudo权限管理
CentOS7.6下安装的OpenLDAP是2.4.44 ,schema目录下并没有sudo.ldif以及sudo.schema文件,需要单独处理。 sudo是默认安装的,sudo相关目录下有sudo.schema模板文件schema.OpenLDAP
find / -name schema.OpenLDAP -exec cp {} /etc/openldap/schema/sudo.schema \;
# 生成sudo.ldif
echo 'include /etc/openldap/schema/sudo.schema' > /tmp/sudo.conf
mkdir /tmp/sudo
slaptest -f /tmp/sudo.conf -F /tmp/sudo
vim /tmp/sudo/cn=config/cn=schema/cn={0}sudo.ldif
替换(前3行)
dn: cn={0}sudo
objectClass: olcSchemaConfig
cn: {0}sudo
为
dn: cn=sudo,cn=schema,cn=config
objectClass: olcSchemaConfig
cn: sudo
删除(最后7行)
structuralObjectClass: olcSchemaConfig
entryUUID: ec3b659a-31a9-1039-90ae-87c69280e4a2
creatorsName: cn=config
createTimestamp: 20190703064542Z
entryCSN: 20190703064542.945991Z#000000#000#000000
modifiersName: cn=config
modifyTimestamp: 20190703064542Z
cp /tmp/sudo/cn=config/cn=schema/cn={0}sudo.ldif /etc/openldap/schema/sudo.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/sudo.ldif
rm -f /tmp/sudo.conf /tmp/sudo
[root@openldap-server ~]# find / -name schema.OpenLDAP -exec cp {} /etc/openldap/schema/sudo.schema \;^C
[root@openldap-server ~]# echo 'include /etc/openldap/schema/sudo.schema' > /tmp/sudo.conf
[root@openldap-server ~]# mkdir /tmp/sudo
[root@openldap-server ~]# slaptest -f /tmp/sudo.conf -F /tmp/sudo
config file testing succeeded
[root@openldap-server ~]# vim /tmp/sudo/cn=config/cn=schema/cn={0}sudo.ldif
[root@openldap-server ~]# vim /tmp/sudo/cn=config/cn=schema/cn={0}sudo.ldif
[root@openldap-server ~]# cp /tmp/sudo/cn=config/cn=schema/cn={0}sudo.ldif /etc/openldap/schema/sudo.ldif
[root@openldap-server ~]# ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/sudo.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "cn=sudo,cn=schema,cn=config"
[root@openldap-server ~]# rm -rf /tmp/sudo.conf /tmp/sudo
[root@openldap-server ~]# ldapadd -x -W -D "cn=Manager,dc=devopstack,dc=com" -f SUODers.ldif
Enter LDAP Password:
adding new entry "ou=SUDOers,dc=devopstack,dc=com"
adding new entry "cn=defaults,ou=SUDOers,dc=devopstack,dc=com"
#将上面的demo(test01)账户配置为sudo权限
这里配置一个运维sudo role,名称为sudo_ops_role,简单配置为sudo 到root所有权限,并将test01加入该role
[root@openldap-server ~]# cat sudo_ops_role.ldif
dn: cn=sudo_ops_role,ou=SUDOers,dc=devopstack,dc=com
objectClass: sudoRole
cn: sudo_ops_role
sudoOption: !authenticate
sudoRunAsUser: root
sudoCommand: ALL
sudoHost: ALL
sudoUser: test01
[root@openldap-server ~]# ldapadd -x -W -D "cn=Manager,dc=devopstack,dc=com" -f sudo_ops_role.ldif
Enter LDAP Password:
adding new entry "cn=sudo_ops_role,ou=SUDOers,dc=devopstack,dc=com"
客户端增加如下配置
vim /etc/nsswitch.conf
# 追加内存
sudoers: files ldap
mv /etc/sudo-ldap.conf{,.bak}
vi /etc/sudo-ldap.conf
uri ldap://192.168.123.23/
base dc=devopstack,dc=com
sudoers_base ou=SUDOers,dc=devopstack,dc=com
验证
8 配置LDAP使用公钥(publicKey)远程ssh登录客户主机
openldap服务端配置
# 安装openssh-ldap
yum install openssh-ldap
# 查看
rpm -aql |grep openssh-ldap
/usr/share/doc/openssh-ldap-7.4p1
/usr/share/doc/openssh-ldap-7.4p1/HOWTO.ldap-keys
/usr/share/doc/openssh-ldap-7.4p1/ldap.conf
/usr/share/doc/openssh-ldap-7.4p1/openssh-lpk-openldap.ldif
/usr/share/doc/openssh-ldap-7.4p1/openssh-lpk-openldap.schema
/usr/share/doc/openssh-ldap-7.4p1/openssh-lpk-sun.ldif
/usr/share/doc/openssh-ldap-7.4p1/openssh-lpk-sun.schema
# 配置添加相关schema
cp /usr/share/doc/openssh-ldap-7.4p1/openssh-lpk-openldap.ldif /etc/openldap/schema/
cp /usr/share/doc/openssh-ldap-7.4p1/openssh-lpk-openldap.schema /etc/openldap/schema/
# 添加
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/openssh-lpk-openldap.ldif
# 账户添加objectClass: ldapPublicKey 并添加属性sshPublicKey
# 具体修改流程,可以使用下面安装的ldapadmin或者phpldapadmin进行配置
objectClass: ldapPublicKey
sshPublicKey: 值是具体的publickey
客户主机配置
# 安装
yum install openssh-ldap
cp /usr/share/doc/openssh-ldap-7.4p1/ldap.conf /etc/ssh/
# 如果使用TLS 配置TLS,这里不使用
vim /etc/ssh/ldap.conf
ssl no
uri ldap://192.168.123.23/
vim /etc/ssh/sshd_config
# 脚本将从LDAP获取密钥并将其提供给SSH服务器
AuthorizedKeysCommand /usr/libexec/openssh/ssh-ldap-wrapper
AuthorizedKeysCommandUser nobody
PubkeyAuthentication yes
登录验证
9 禁止匿名访问
默认情况下匿名用户可以获取所有用户信息,甚至是密码字段,虽然密码字段是经过加密的那也很危险
创建disable_anon.ldif文件
dn: cn=config
changetype: modify
add: olcDisallows
olcDisallows: bind_anon
dn: cn=config
changetype: modify
add: olcRequires
olcRequires: authc
dn: olcDatabase={-1}frontend,cn=config
changetype: modify
add: olcRequires
olcRequires: authc
导入配置
ldapadd -Q -Y EXTERNAL -H ldapi:/// -f disable_anon.ldif
10 设置ACL
拒绝所有用户查看用户信息,并且添加有ldap管理账号
创建acl.ldif
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcAccess
olcAccess: to attrs=userPassword
by anonymous auth
by dn.base="cn=ldapadmin,ou=manage,dc=taovip,dc=com" write
by * none
olcAccess: to *
by anonymous auth
by dn.base="cn=ldapadmin,ou=manage,dc=taovip,dc=com" write
by dn.base="cn=ldapread,ou=manage,dc=taovip,dc=com" read
by * none
导入配置
ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f acl.ldif
删除ACL
创建文件del_acl.ldif
dn: olcDatabase={2}hdb,cn=config
changetype: modify
delete: olcAccess
olcAccess: {0}
导入配置
ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f acl.ldif
11 创建管理用户
创建add_ou.ldif
dn: ou=manage,dc=devopstack,dc=com
ou: manage
description: Directory Manage
objectClass: top
objectClass: organizationalUnit
创建add_manage_user.ldif
n: cn=ldapadmin,ou=manage,dc=devopstack,dc=com
cn: ldapadmin
sn: ldapadmin
uid: ldapadmin
objectClass: top
objectClass: shadowAccount
objectClass: inetOrgPerson
objectClass: organizationalPerson
objectClass: person
userPassword:{SSHA}16ZF0nlRiQPyhJVVLy9KSnwktv0Mkd7q
dn: cn=ldapread,ou=manage,dc=devopstack,dc=com
cn: ldapread
sn: ldapread
uid: ldapread
objectClass: top
objectClass: shadowAccount
objectClass: inetOrgPerson
objectClass: organizationalPerson
objectClass: person
userPassword: {SSHA}16ZF0nlRiQPyhJVVLy9KSnwktv0Mkd7q
导入配置
ldapadd -x -D cn=root,dc=example,dc=com -W -f add_ou.ldif
ldapadd -x -D cn=root,dc=example,dc=com -W -f add_manage_user.ldif
12 OpenLDAP限制用户登录系统
有些情况下,不能让每个用户都能登录系统,所以要限制用户登录。
在/etc/pam.d/sshd中加入pam_access.so模块
account required pam_access.so
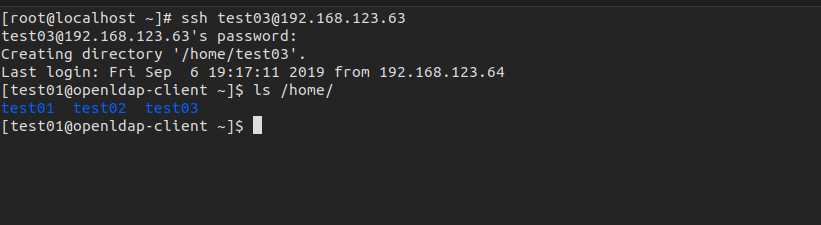
编辑/etc/security/access.conf 这里限制test03用户ssh登录系统
tail -1 /etc/security/access.conf
- : test03 : ALL
无需重启服务:
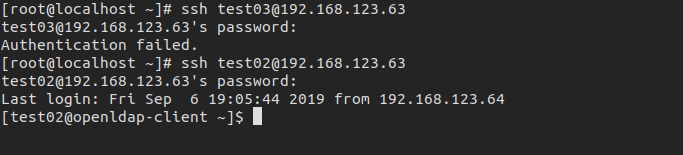
如图 test03已经不能登录服务器了,test02还是可以登录的。
13 OpenLDAP 强制用户登录系统更改密码
在LDAP中,默认情况下用户无权修改自己的密码,如果用户自行修改密码,会遇到Result: Insufficient access (50)的错误,因此我们需要打开用户修改自己密码的权限。
14 OpenLDAP的主从
14.1 服务器规划
| ip | hostname | 角色 | 备注 |
|---|---|---|---|
| 192.168.123.23 | openldap-server | openLdap, httpd, phpldapadmin | 主节点 |
| 192.168.123.64 | openldap-server02 | openLdap, httpd, phpldapadmin | 从节点 |
| 192.168.123.63 | openldap-client | openLdap client | client端 |
14.2 配置OpenLDAP主从结构
14.2.1 主节点添加模块syncprov
vim mod_syncprov.ldif
dn: cn=module,cn=config
objectClass: olcModuleList
cn: module
olcModulePath: /usr/lib64/openldap
olcModuleLoad: syncprov.la
# 发送配置使之生效
ldapadd -Y EXTERNAL -H ldapi:/// -f mod_syncprov.ldif
vim syncprov.ldif
dn: olcOverlay=syncprov,olcDatabase={2}hdb,cn=config
objectClass: olcOverlayConfig
objectClass: olcSyncProvConfig
olcOverlay: syncprov
olcSpSessionLog: 100
# 发送配置使之生效
ldapadd -Y EXTERNAL -H ldapi:/// -f syncprov.ldif
14.2.2 从节点配置同步
需要根据实际情况修改的参数:
provider 同步来源,也就是主节点,可以包含多个主节点
binddn 主节点管理账户
credentials 主节点管理账户密码
searchbase 根目录
vim syncrepl.ldif
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcSyncRepl
olcSyncRepl: rid=001
provider=ldap://192.168.123.23:389/
bindmethod=simple
binddn="cn=Manager,dc=devopstack,dc=com"
credentials=123456
searchbase="dc=devopstack,dc=com"
scope=sub
schemachecking=on
type=refreshAndPersist
retry="30 5 300 3"
interval=00:00:05:00
# 发送配置使之生效
ldapadd -Y EXTERNAL -H ldapi:/// -f syncrepl.ldif
14.2.3 验证主从同步情况
从服务节点验证数据是否同步正常
ldapsearch -x -b 'ou=People,dc=devopstack,dc=com'
14.2.4 远程主机配置(客户端)
authconfig --enableldap --enableldapauth --ldapserver="192.168.123.23,192.168.123.64" --ldapbasedn="dc=devopstack,dc=com" --update
15 openldap服务双主模式(镜像模式)
15.1 服务器规划
| ip | hostname | 角色 | 备注 |
|---|---|---|---|
| 192.168.123.23 | openldap-server | openLdap, httpd, phpldapadmin | server端 |
| 192.168.123.64 | openldap-server02 | openLdap, httpd, phpldapadmin | server端 |
| 192.168.123.63 | openldap-client | openLdap client | client端 |
15.2 配置OpenLDAP 双主结构(mirrormode)
OpenLDAP的2个主节点都需要添加模块syncprov
vim mod_syncprov.ldif
dn: cn=module,cn=config
objectClass: olcModuleList
cn: module
olcModulePath: /usr/lib64/openldap
olcModuleLoad: syncprov.la
# 发送配置使之生效
ldapadd -Y EXTERNAL -H ldapi:/// -f mod_syncprov.ldif
vim syncprov.ldif
dn: olcOverlay=syncprov,olcDatabase={2}hdb,cn=config
objectClass: olcOverlayConfig
objectClass: olcSyncProvConfig
olcOverlay: syncprov
olcSpSessionLog: 100
# 发送配置使之生效
ldapadd -Y EXTERNAL -H ldapi:/// -f syncprov.ldif
15.3 主节点1配置(192.168.123.23)同步
需要根据实际情况修改的参数:
provider 同步来源,也就是主节点,可以包含多个主节点
binddn 主节点管理账户
credentials 主节点管理账户密码
searchbase 根目录
特别主机:2个主节点属性 olcServerID的值不能相同,provider指向对方
[root@localhost ~]# cat master_node_1.ldif
dn: cn=config
changetype: modify
replace: olcServerID
olcServerID: 0
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcSyncRepl
olcSyncRepl: rid=001
provider=ldap://192.168123.64:389/
bindmethod=simple
binddn="cn=Manager,dc=devopstack,dc=com"
credentials=123456
searchbase="dc=devopstack,dc=com"
scope=sub
schemachecking=on
type=refreshAndPersist
retry="30 5 300 3"
interval=00:00:05:00
-
add: olcMirrorMode
olcMirrorMode: TRUE
dn: olcOverlay=syncprov,olcDatabase={2}hdb,cn=config
changetype: add
objectClass: olcOverlayConfig
objectClass: olcSyncProvConfig
olcOverlay: syncprov
# 发送配置使之生效
ldapadd -Y EXTERNAL -H ldapi:/// -f master_node_1.ldif
15.4 主节点2配置(192.168.123.64)同步
vim master_node_2.ldif
dn: cn=config
changetype: modify
replace: olcServerID
olcServerID: 2
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcSyncRepl
olcSyncRepl: rid=001
provider=ldap://192.168.123.23:389/
bindmethod=simple
binddn="cn=Manager,dc=devopstack,dc=com"
credentials=123456
searchbase="dc=devopstack,dc=com"
scope=sub
schemachecking=on
type=refreshAndPersist
retry="30 5 300 3"
interval=00:00:05:00
-
add: olcMirrorMode
olcMirrorMode: TRUE
dn: olcOverlay=syncprov,olcDatabase={2}hdb,cn=config
changetype: add
objectClass: olcOverlayConfig
objectClass: olcSyncProvConfig
olcOverlay: syncprov
# 发送配置使之生效
ldapadd -Y EXTERNAL -H ldapi:/// -f master_node_2.ldif
备注:
导入之后的信息在这个位置
/etc/openldap/slapd.d/cn=config/olcDatabase={2}hdb.ldif
15.5 验证服务节点验证数据是否同步正常
验证是否同步
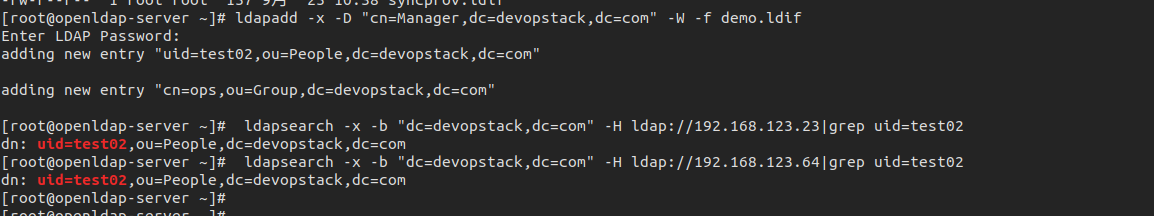
[root@openldap-server ~]# ldapadd -x -D "cn=Manager,dc=devopstack,dc=com" -W -f demo.ldif
Enter LDAP Password:
adding new entry "uid=test02,ou=People,dc=devopstack,dc=com"
adding new entry "cn=ops,ou=Group,dc=devopstack,dc=com"
[root@openldap-server ~]# ldapsearch -x -b "dc=devopstack,dc=com" -H ldap://192.168.123.23|grep uid=test02
dn: uid=test02,ou=People,dc=devopstack,dc=com
[root@openldap-server ~]# ldapsearch -x -b "dc=devopstack,dc=com" -H ldap://192.168.123.64|grep uid=test02
dn: uid=test02,ou=People,dc=devopstack,dc=com
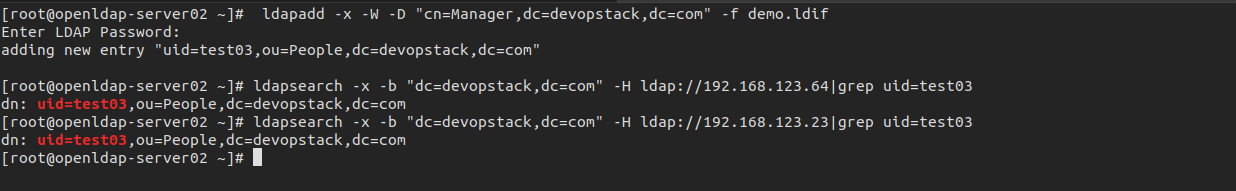
[root@openldap-server02 ~]# ldapadd -x -W -D "cn=Manager,dc=devopstack,dc=com" -f demo.ldif
Enter LDAP Password:
adding new entry "uid=test03,ou=People,dc=devopstack,dc=com"
[root@openldap-server02 ~]# ldapsearch -x -b "dc=devopstack,dc=com" -H ldap://192.168.123.64|grep uid=test03
dn: uid=test03,ou=People,dc=devopstack,dc=com
[root@openldap-server02 ~]# ldapsearch -x -b "dc=devopstack,dc=com" -H ldap://192.168.123.23|grep uid=test03
dn: uid=test03,ou=People,dc=devopstack,dc=com
[root@openldap-server02 ~]#
15.6 客户端配置连接信息
[root@localhost slapd.d]# authconfig --enableldap --enableldapauth --ldapserver="192.168.123.23,192.168.123.64" --ldapbasedn="dc=devopstack,dc=com" --update
16 搭建OpenLDAP自助修改密码系统Self Service Password
配置yum源
cat >> /etc/yum.repos.d/ltb-project.repo << "EOF"
[ltb-project-noarch]
name=LTB project packages (noarch)
baseurl=https://ltb-project.org/rpm/releasever/noarch
enabled=1
gpgcheck=0
gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-LTB-project
EOF
安装self-service-password
yum -y install self-service-password php-ldap php-mcrypt libmcrypt libmcrypt-devel mcrypt mhash
配置apache依赖
cat>/etc/httpd/conf.d/self-service-password.conf << "EOF"
Listen 8888
<VirtualHost *:8888>
ServerAdmin myself.ldap.com
DocumentRoot /usr/share/self-service-password
DirectoryIndex index.php
AddDefaultCharset UTF-8
Alias /ssp /var/www/html/self-service-password
<Directory "/usr/share/self-service-password">
AllowOverride None
Require all granted
</Directory>
LogLevel warn
ErrorLog /var/log/httpd/ssp_error_log
CustomLog /var/log/httpd/ssp_access_log combined
</VirtualHost>
EOF
重启systemctl restart httpd
配置self-service-password 配置文件
vim /usr/share/self-service-password/conf/config.inc.phpldap_url = "ldap://localhost:389 ldap://192.168.123.64:389";
ldap_starttls = false;ldap_binddn = "cn=manager,dc=devopstack,dc=com";
ldap_bindpw = "123456";ldap_base = "dc=devopstack,dc=com";
ldap_login_attribute = "uid";ldap_fullname_attribute = "cn";
ldap_filter = "(&(objectClass=account)(ldap_login_attribute={login}))"; ## 此配置为公司配置,objectClass=account是创建用户自定义的objectClass,要对应上。
mail_from = "admin@example.com";mail_from_name = "Self Service Password";
mail_signature = "";who_change_password = "user"; #用户可修改密码
notify_on_change = true;mail_sendmailpath = '/usr/sbin/sendmail';
mail_protocol = 'smtp';mail_smtp_debug = 0;
mail_debug_format = 'error_log';mail_smtp_host = 'localhost';
mail_smtp_auth = true;mail_smtp_user = '';
mail_smtp_pass = '';mail_smtp_port = 25;
mail_smtp_timeout = 30;mail_smtp_keepalive = false;
mail_smtp_secure = 'tls';mail_smtp_autotls = true;
mail_contenttype = 'text/plain';mail_wordwrap = 0;
mail_charset = 'utf-8';mail_priority = 3;
mail_newline = PHP_EOL;
keyphrase = "dbjbsdojsdb"; ##随机修改,不修改会报错
重启httpd:
systemctl restart httpd
验证:
登录用户修改密码自助平台
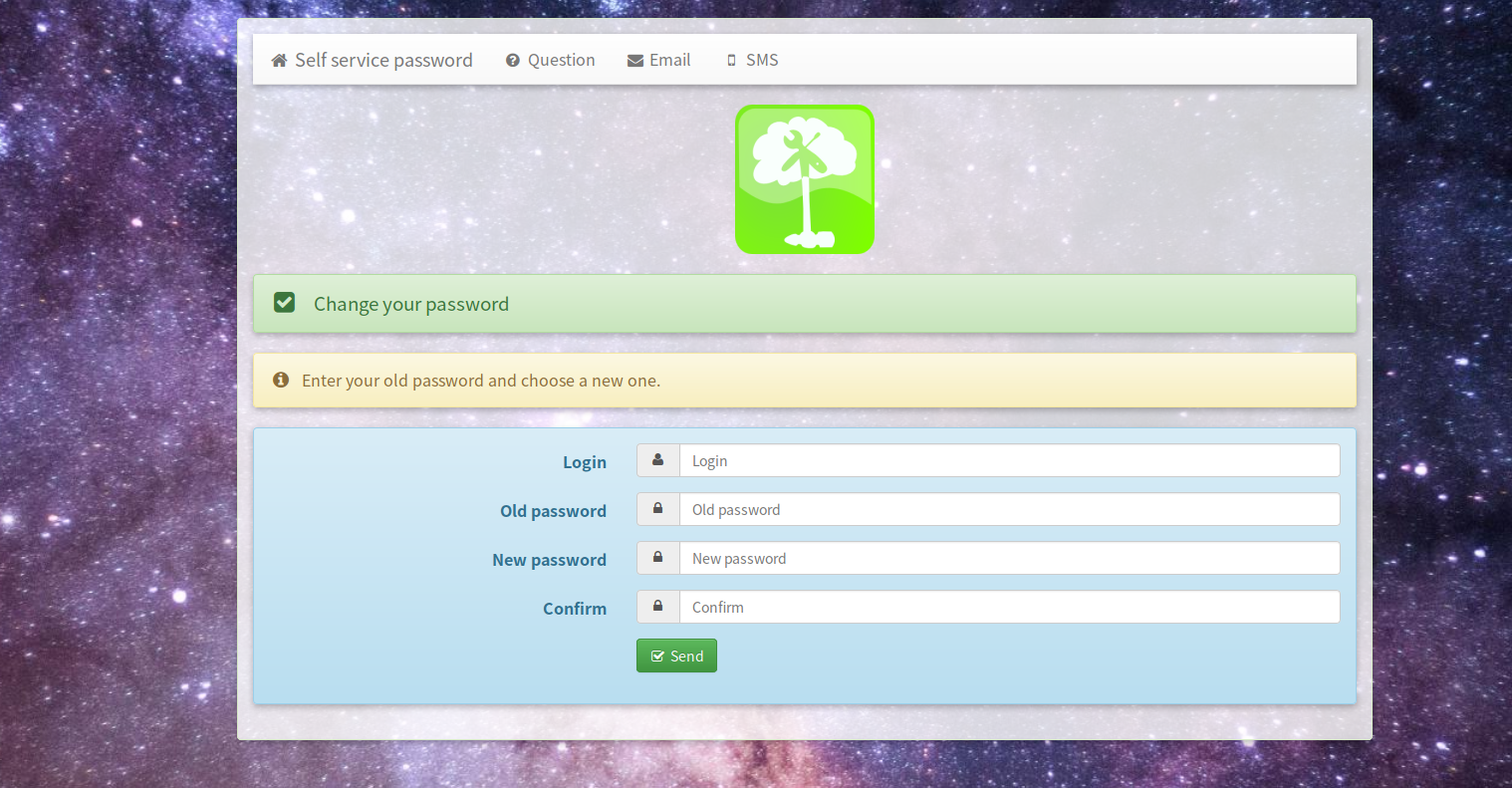
修改方式有四种,我这边只验证了第一种如下图方式修改
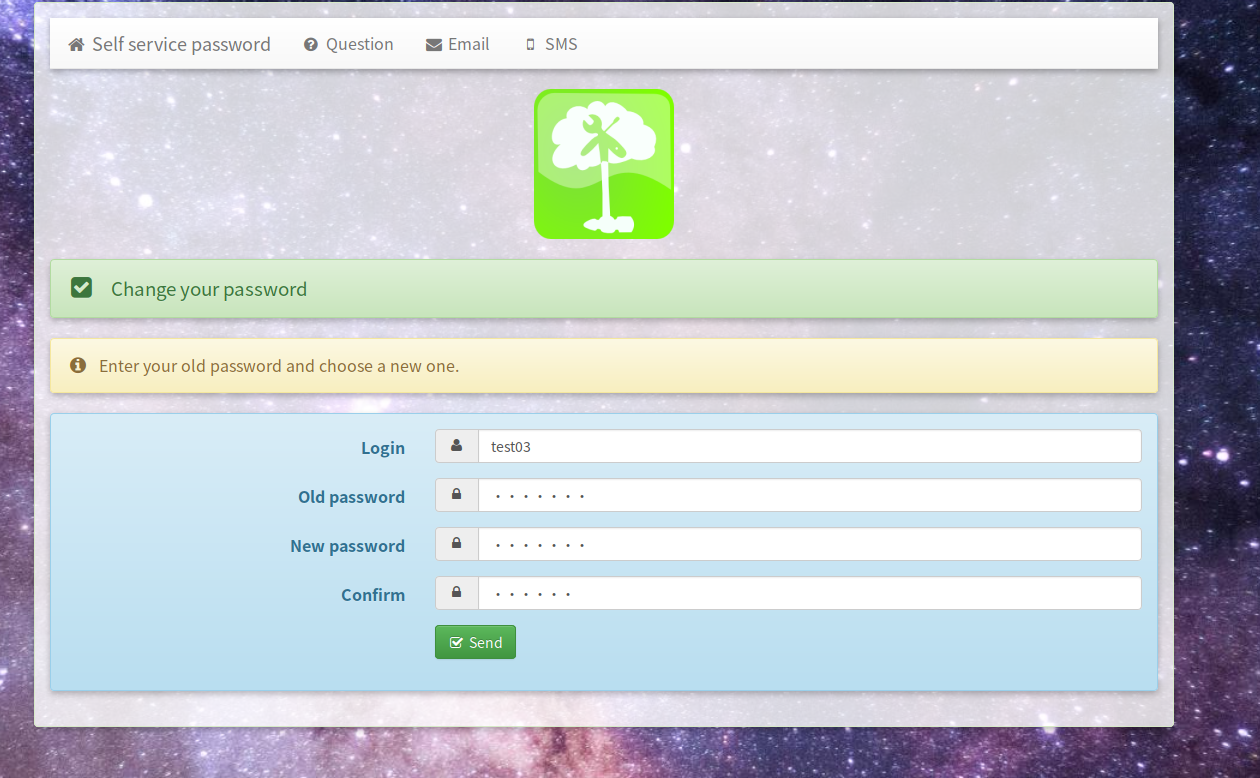
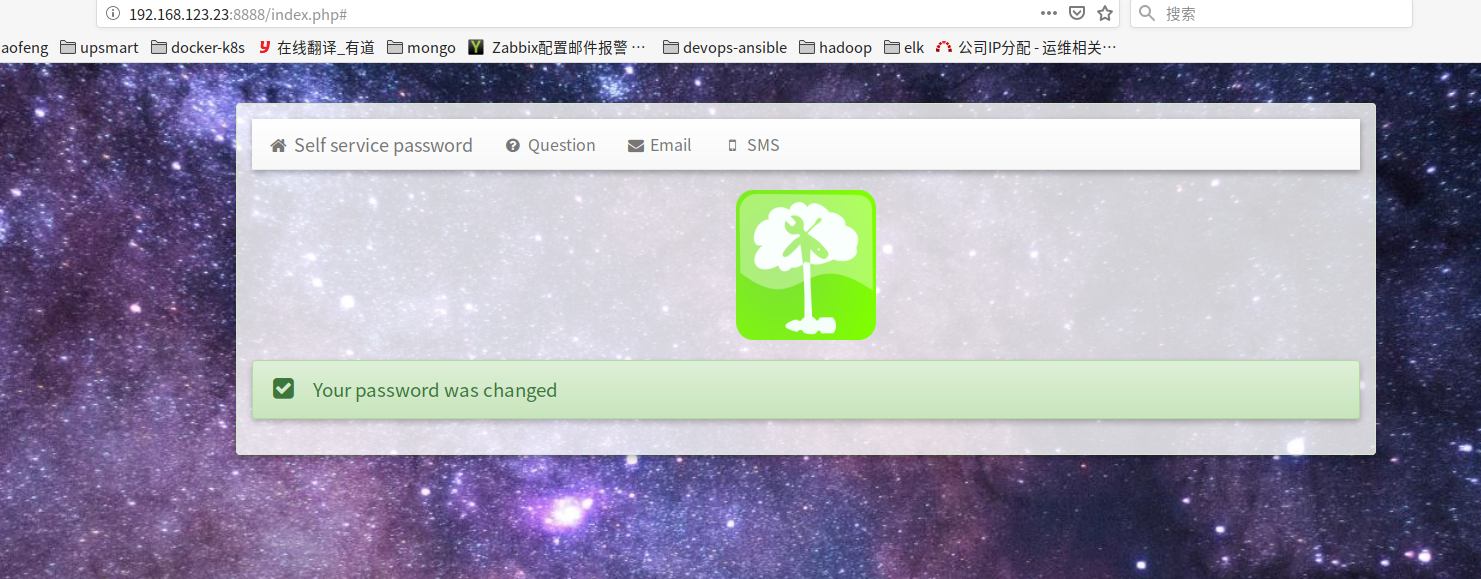
通过登录ssh验证是生效的。
如果修改密码不成功,需修改ldap配置,如下
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcAccess
olcAccess: to attrs=userPassword
by self write
by anonymous auth
by * none
olcAccess: to *
by self write
by users read
by * none
导入配置
ldapmodify -Y EXTERNAL -H ldapi:/// -f updatepass.ldif
17 openldap数据备份与恢复
OpenLDAP 中数据备份有多种备份方式,如通过 slapcat 指令进行备份,通过 phpLDAPadmin 控制台进行备份,通过ldapsearch等方式来进行备份。
17.1 通过slapcat备份
slapcat命令只能在openldap服务器上执行.
[root@openldap-server ~]# slapcat -v -l /srv/ldapbackup_devopstack.ldif
5d8cb159 ldif_read_file: checksum error on "/etc/openldap/slapd.d/cn=config/olcDatabase={2}hdb.ldif"
5d8cb159 The first database does not allow slapcat; using the first available one (2)
# id=00000001
# id=00000002
# id=00000003
# id=00000004
# id=00000007
# id=00000008
# id=0000000d
# id=0000000e
# id=0000000f
# id=00000010
备注:会有checksum error,这个不用管,我们手动修改了文件肯定checksum不对了。
17.2 通过ldapsearch方式备份
ldapsearch -x -D "cn=Manager,dc=devopstack,dc=com" -w "123456" -b 'dc=devopstack,dc=com' -LLL -H ldap://192.168.123.23 > ldapbackup_devopstack.ldif
查看
[root@openldap-server ~]# head ldapbackup_devopstack.ldif
dn: dc=devopstack,dc=com
o: devopstack com
dc: devopstack
objectClass: top
objectClass: dcObject
objectClass: organization
dn: cn=Manager,dc=devopstack,dc=com
objectClass: organizationalRole
cn: Manager
可以写成脚本的形式通过crontab自动备份。
17.3 恢复openldap数据
现在我们来恢复openldap数据,这里面有一点一定要注意的是,我们恢复的openldap数据,一定是在原来openldap服务所在的服务器上。
模拟数据丢失
# 获取所有用户配置条目
ldapsearch -x -Z -LLL -H ldap://192.168.123.23 -b 'ou=People,dc=devopstack,dc=com' | wc -l
37
# 清空所有所有条目
ldapdelete -x -D "cn=manager,dc=devopstack,dc=com" -w 123456 -r "dc=devopstack,dc=com"
# 确认条目
ldapsearch -x -Z -LLL -H ldap://172.16.10.220 -b 'ou=People,dc=laoshiren,dc=com' | wc -l
0
还原数据
systemctl stop slapd && systemctl status slapd
# 清空原openldap数据
rm -fr /var/lib/ldap/*
/usr/sbin/slapadd -l /data/ldap_backups/ldap-20190109-21.ldif
# 输出
/usr/sbin/slapadd -l /srv/ldapbackup_devopstack.ldif
5d8cb3aa ldif_read_file: checksum error on "/etc/openldap/slapd.d/cn=config/olcDatabase={2}hdb.ldif"
5d8cb3aa The first database does not allow slapadd; using the first available one (2)
5d8cb3aa hdb_db_open: warning - no DB_CONFIG file found in directory /var/lib/ldap: (2).
Expect poor performance for suffix "dc=devopstack,dc=com".
_#################### 100.00% eta none elapsed none fast!
Closing DB...
# 拷贝数据配置文件
cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
# 赋权
chown ldap:ldap -R /var/lib/ldap/
# 启动 slapd
systemctl start slapd && systemctl status slapd
验证
[root@openldap-server ~]# ldapsearch -x -Z -LLL -H ldap://192.168.123.23 -b 'ou=People,dc=devopstack,dc=com' | wc -l
37
已恢复。
- 我的微信
- 这是我的微信扫一扫
-

- 我的微信公众号
- 我的微信公众号扫一扫
-